In the era of information technology, the cyber threat is constantly increasing. Cyberattacks are among the biggest challenges faced by organizations and companies, as they pose a serious threat to the security and safety of digital systems.
In this article, we aim to review the types of cyber crime and shed light on the importance of detecting and confronting them to ensure the safety of systems and data.
Introduction:
What is the definition of cyber crime?
Cyber crime refers to deliberate and organized operations that target the vulnerabilities and weaknesses in information systems and electronic networks with the aim of obtaining secret information, manipulating data, causing harm to systems, or disrupting available services.
Some key objectives of cyber crime:
The objectives of cyber crime can be diverse and vary depending on the attacker, motives, and end goals. However, some key objectives of cyber attacks can be identified, including:
- Information theft: Some cyber attacks primarily aim to steal sensitive information, such as financial information, intellectual property, and personal information, which can be exploited for illegal purposes like financial fraud or extortion.
- Service disruption: Some attackers aim to disrupt critical services, whether at the organizational or critical infrastructure level, leading to the shutdown of websites and disabling essential services for companies and entities.
- Industrial espionage: Some attackers use cyber attacks to spy on competitors or other countries to obtain sensitive information related to technological innovations or business strategies.
- Infrastructure destruction: Some attackers aim to destroy the infrastructure of organizations, government systems, or critical infrastructure, causing disruption to vital operations and essential services.
- Manipulation of information and data: The goal of some cyber attacks may involve manipulating, distorting, or unauthorized modification of data in unauthorized ways.
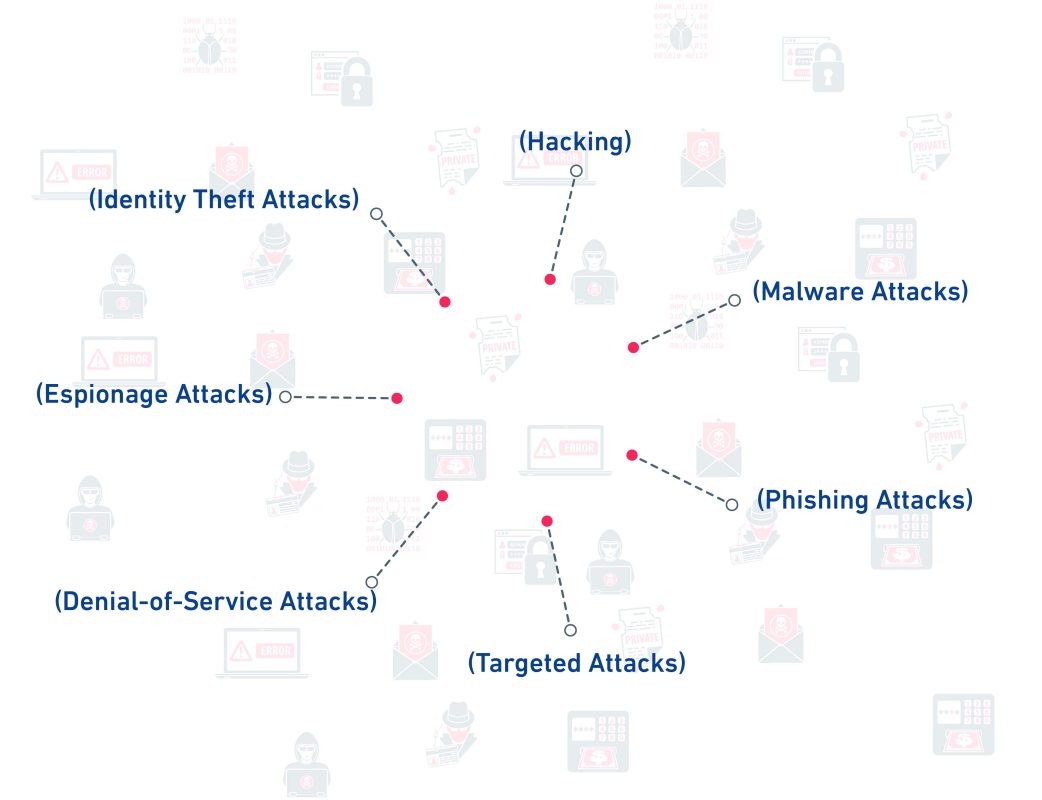
Now, what are the common types of cyber crime?
Here are examples of common types of cyber crime :
- Hacking attacks: These include attempts to breach computer systems and networks by attackers to gain unauthorized access, modify, delete, or use confidential information in illegal ways.
- Malware attacks: These attacks are a one types of cyber crime and include viruses, Trojan horses, spyware, ransomware, and other malicious software that infiltrate systems and cause damages such as device disablement, data theft, or activity surveillance.
- Phishing attacks: These attacks target personal and sensitive information, such as passwords and banking account details, through deceptive emails and fake web pages that appear to be from trusted sources.
- Targeted attacks: These attacks specifically target selected individuals or entities, and customized attacks are developed to bypass security measures and gain access to sensitive information.
- Denial-of-service attacks: These attacks aim to disable or restrict network services or systems by increasing traffic or overwhelming them with a large volume of requests, resulting in service disruption for legitimate users.
- Espionage attacks: These attacks target the theft of sensitive information and espionage on network systems and infrastructure with the purpose of obtaining secret information for commercial or political purposes.
- Identity theft attacks: one of the most well-known types of cyber crime , it aims to steal personal identities with the purpose of obtaining sensitive information or using it for illegal activities.
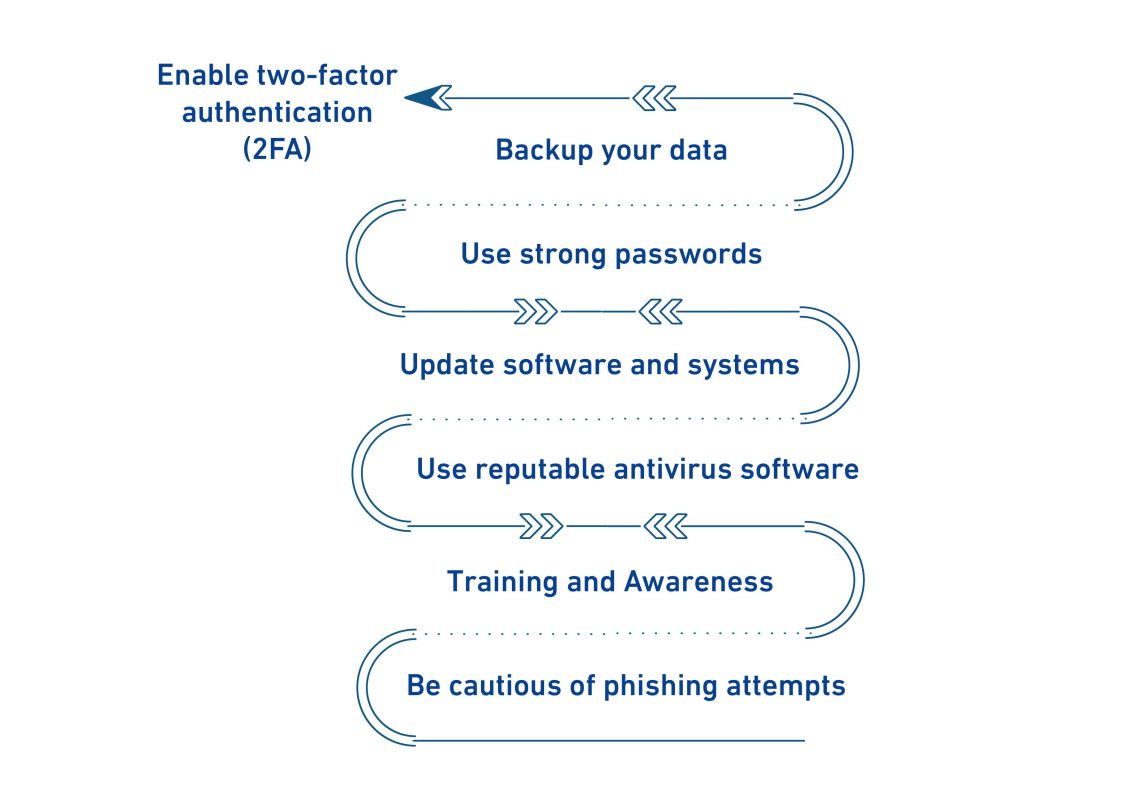
How can we protect ourselves and our organizations from different types of cyber crime?
To protect ourselves and our organizations from various types of cyber crime , effective security measures should be taken. Here are some general guidelines for protecting against cyber crime:
- Update software and systems: Necessary security updates should be installed, and software and systems should be regularly updated. It is also important to apply cybersecurity controls to sensitive systems, especially for government entities and all owners or operators of sensitive systems. Renad Al Majd Information Technology Company can assist you in implementing all applicable controls.
- Use strong passwords: strong and unique passwords should be used for each account or system. Passwords.
- Be cautious of phishing attempts: Be vigilant when it comes to suspicious emails, messages, or websites that request personal or sensitive information. Avoid clicking on links or downloading attachments from unknown sources.
- Use reputable antivirus software: Install and regularly update reliable antivirus software to detect and remove malware from your systems.
- Enable two-factor authentication (2FA): Enable 2FA whenever possible to add an extra layer of security to your accounts. This typically requires a second verification step, such as a code sent to your mobile device, in addition to your password.
- Backup your data: regularly backup your important data and files to an external device or secure cloud storage. This ensures that you have a copy in case of data loss or a ransomware attack.
- Training and Awareness: Employees must be educated about the importance of cybersecurity and taught good security practices, through the engagement of trusted companies that offer workshops and training courses for cybersecurity awareness, such as Renad Al-Majd Information Technology Company. This includes not sharing personal information or passwords with others and reporting any suspicious activity or potential attacks.
- Implement network security measures: utilize firewalls, intrusion detection systems, and other network security tools to protect your systems from unauthorized access and suspicious activities.
- Monitor your systems: Regularly monitor your networks, systems, and logs for any unusual or suspicious activity. Implement real-time monitoring and incident response mechanisms to detect and respond to cyber attacks promptly.
- Develop a cybersecurity incident response plan: Create a comprehensive incident response plan that outlines the steps to be taken in the event of a cyberattack. This should include reporting the incident, isolating affected systems, and engaging appropriate cybersecurity professionals to mitigate the damage.
Conclusion:
Cyber crime poses a significant threat to individuals, organizations, and societies at large. Understanding the types of cyber crime and implementing effective security measures are crucial for protecting against these threats. By staying informed, adopting best prFactices, and investing in cybersecurity measures, we can better defend ourselves and our organizations against cybercrime and ensure the safety and integrity of our digital systems, and data.
You can improve cybersecurity and security with the help of RMG services, protecting the continuity and integrity of digital systems.